ALERT: Log4j is the Most Dangerous Vulnerability in Recent History and Your Business Needs to Act NOW

Recently, a vulnerability was discovered that will affect all computer users, whether you’re a private user or a business. This situation might take some time to resolve so we want you to know everything you need to know about Log4j so that you can protect yourself. What is Log4j? Log4j is a Java library, which […]
Twitch Creator Information Exposed After Hack

Amazon’s popular streaming service, Twitch, which allows content creators and gamers to broadcast their gaming for their audiences, has recently suffered a data breach. This breach revealed how much money some huge creators make and exposed another huge issue that Amazon needs to take care of. Let’s learn more about this Twitch hacking. ZDNet reported, […]
MosaicLoader Malware Uses Cracked Software to Steal Your Credentials

While most threats make themselves instantly known on your device as soon as they install themselves, such as ransomware and malware, others don’t. The newest discovered threat, MosiacLoader, is one of these that quietly installs itself in the background of your device and causes issues behind the scenes before you realize it’s even there. BitDefender […]
Windows Suffering from MSHTML Exploit

Kaspersky has recently tracked and discovered a vulnerability within Microsoft’s MSHTML browser engine. This vulnerability is being exploited all over the world, so what can you do to avoid it, and can it affect your business? What is MSHTML? Within the server unit and personal computer version of windows, MSHTML is the browser engine. If […]
Learning Telltale Signs of a Phishing Email Can Save Your Business

We know you’ve heard of phishing by now, and this threat is getting bigger and bigger as time passes. With this growth, phishing attacks are becoming harder than ever to identify. Sometimes, it can be really hard for businesses to tell the difference between phishing scams and actual emails. Today, we’re going to look at […]
The Most Popular Subject Lines for Phishing Threats are Revealing

A well-placed and timed phishing email can trick even the best and most cautious employees. Today we’re going to be taking a look at what makes these tricks successful and what subject lines you should be watching out for in a common phishing email. You might be shocked at the results that were found in […]
Security For Law Firms: MyTek Goes Over The Basics

When it comes to tradition, security and new technology can easily be overlooked, even if it is crucial, or at least really important. One industry that is deeply immersed in tradition is the modern law firm, even though this is an industry that relies heavily on data, technology and security. Today we’re going to be […]
Tip of the Week: Examining NIST’s Definition of Zero Trust

How many people do you trust? This is a pretty difficult question, but luckily, in a zero trust network, that question is answered for you. The idea of this network is that everyone, no matter who they are, needs to be verified. You might imagine that this has been effective in preventing breaches. But what […]
Web Browser Security Is So Important
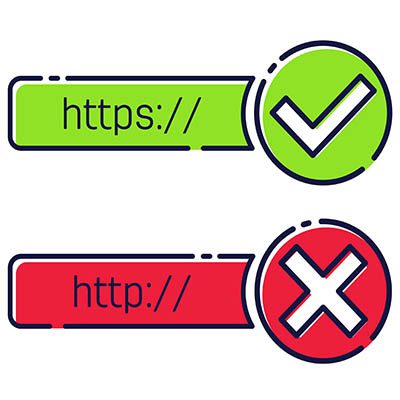
Even though you may not realize it, the internet browser is one of the most-used applications in today’s world of cloud-hosted resources and online content. Though even though you use it so often, for almost everything you do in the day, is it secure enough? In some ways it is, but in others… it could […]
Could Voice Authentication Join the Ranks of MFA?

Authentication has been such a huge topic in the past few years, especially with the increase in data and security. Because of the increased importance of security, people are looking at voice automation, to see if it could be used for security. Today we’re going to look at how it could actually be promising. First […]