Welcome to
MyTek IT Blog
MyTek has been serving the Arizona area since 2009, providing Phoenix IT Support such as technical helpdesk support, computer support, and technology consulting to growing Phoenix businesses. As part of that commitment we have put together the MyTek IT blog.
We work hard to stay up-to-date on the ever changing business technology landscape to ensure you get the most advanced and high quality service from us. That is why we have this blog to help you keep a pulse on what is going on in the information technology world, but also anything that will help your business run smoother.
Below you can view the most recent blog posts covering everything from information technology to business strategies and so much more!
Unified communications can help your team work together. This might mean nothing to you at the moment, but in this article we’re …
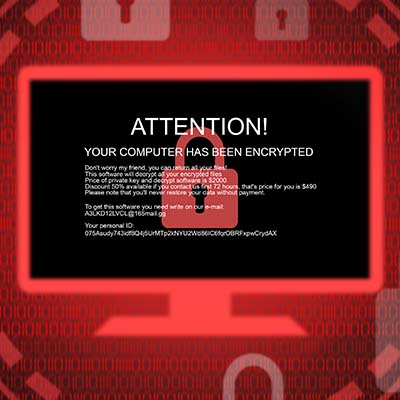
Ransomware is one of the worst modern cyberattacks and we can support this claim. These attacks and their impacts have devastated businesses …
There are some essential best practices that your business should be following. Today, we’ve rounded up all of the most important practices …
When you’re writing an email, do you use the CC and BCC functions? Even if you have used these fields before, you …
Within the past few years, remote work has been on the uprise, due to the pandemic first, but then due to the …
As we’re sure you already know, Microsoft has become a juggernaut in the increasingly competitive business world with its countless solutions for …
Did you know that not working (well at least taking a break) is essential for your mental well-being? Whether you are a …
Server problems are just plain crippling. Your business server handles a lot of crucial data for your organization. Over the years, it …
Cards are a standard mode of payment these days. We end up using credit/debit cards while shopping online or offline all the …
Your employee’s health is paramount. Happy employees are more productive, engaged, and punctual in performing their duties. They contribute positively to your …
MyTek’s Phoenix Tech Services Tip of the Week – How to Effectively Use Google
Google is the most visited website in the world. That distinction doesn’t come easily as 4.2 billion people are active users of …
Cybersecurity is a critical part of managing any business. This is especially true nowadays when there are countless individuals and organizations formed …
In many ways, social media is the defining characteristic of the information age. It has transformed the way people communicate, market their …
What does a frustrating morning at work look like? You reach the office on time, ready to work, you turn on your …
Phoenix IT Solutions Include Automation to Rejuvenate Productivity
There are some cases where productivity is a challenge, especially in the case where you’re being asked to work on something repetitive …
What exactly is PII? It refers to information that may be used to identify a person. And, while we’re on the subject …
Every week, MyTek provides local companies with technology solutions. The topic for this week is passwords. Passwords are usually a big source …